Averting Modern Telecom Scams: Fraud Prevention in a VoIP World
The telecom sector has seen unprecedented growth in the last 20 years. In the past year alone, the global telecom market grew by a staggering $158 billion. But as the industry grows, the challenges increase as well.
By its design, the telecom sector has become the target of scams and other malicious activities. These scams grow in complexity yearly as hackers find news to exploit an ever-evolving architecture.
According to a report by the Communications Fraud Control Association (CFCA), VOIP fraud grew at an alarming rate of 29%. But, all hope is not lost. Cybersecurity firms and related firms find news to combat malicious activity.
Industry experts have devised new and complex methods to detect anomalies and combat telecom scams. Here, we’ll explore several different kinds of scams that plague the telecom sector today. Additionally, we’ll highlight techniques that the industry uses (and can use) to combat VOIP fraud.
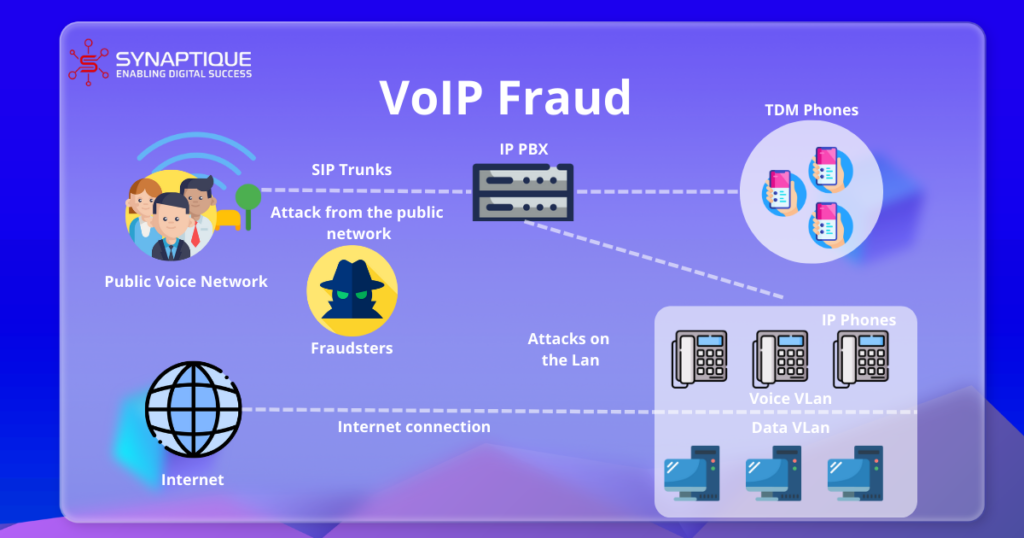
Tracking the Numbers: How VOIP Fraud Is on the Rise
VOIP architecture is built for high accessibility and cost-efficiency. The very reason that anyone can use it at a low cost is why scammers find it the most convenient. Vishing attacks, a popular scam that exploits VOIP, surged by over 500% in 2021.
The financial sector seems to be the primary target, accounting for almost half of all VOIP fraud. But, it’s not alone. Studies show government imposter scams that exploit VOIP have also surged in the past few years. Just in the U.S. alone, consumer losses related to government imposter scams reached almost $440 million in 2020.
But developed regions such as the U.S. are not the only target. Developing nations such as India, Brazil, Bangladesh, Ghana, Indonesia, etc., are prime targets for VOIP fraud. Insights show developing nations are more prone to VOIP fraud when compared to developed nations.
VOIP Scams in a VOIP World
- Voicemail Hacking/Call Transfer Schemes
Voicemail hacking schemes involve hackers gaining access to a user’s voicemail system. Once access is gained, they start charging the user in various ways. For example, the hacker performs collect calls and accepts the charges on the user’s behalf.
A more advanced voicemail hacking method involves charging a malicious service provider linked to the hacker. Because the hacker has access to the user’s voicemail system, the hacker can charge certain fees on the user’s behalf. The fee is then collected by the service provider linked to the hacker.
- Bypass Fraud
Bypass fraud exploits VOIP architecture to make it seem like an international call is a local one. Sim Boxing, Landing Fraud, and Grey Boxing are other terms typically used to refer to Bypass fraud.
The primary target of Bypass Fraud is telecom operators. Such operators lose out on revenue that they would typically collect through termination and interconnection costs.
Hackers use sim boxes to manipulate payment methods in the eyes of telecom operators.
To the operator, it seems as if the call is domestic. Thus, local service providers are manipulated into believing a call is domestic.
Given the nature of the scam, countries where international calls cost more than local calls are the primary target. In African countries, an estimated $2 billion is lost annually to bypass fraud. Ghana, a popular target of bypass fraud, reportedly loses $5.8 million in taxes annually.
- Access Stimulation Schemes
Access stimulation schemes, also known as traffic pumping schemes, are carried out by two or more local carriers than arrange what to charge callers. The carriers exploit callers by charging them higher rates than they would typically be paying.
To pull this off, a carrier with a high volume of incoming calls diverts those calls to another page that charges premium rates. The caller unknowingly connects with a carrier charging needlessly high rates. In the process, the carriers benefit from the extra amount, distributed amongst themselves based on their internal arrangement.
In another context, access stimulation also involves carriers using the same scheme of inflating incoming calls. But here, the purpose is to benefit from compensation fees that regulatory authorities must pay.
Access stimulation/traffic pumping is illegal as callers unknowingly charge premium rates.
- False Answer Supervision (FAS)
False Answer Supervision (FAS) is a type of VOIP fraud where the service provider bills the caller more than the actual amount. The billed amount falsely adds more time to the call duration.
In many cases, the party responsible for the fraud might only add a few seconds to each call. Of course, the caller might not notice a few seconds added. But, add up the extra few seconds against a large number of similarly charged callers. The result is a large amount of additional revenue that the service provider can bring in.
Another scenario is where the service provider keeps the caller on hold. The caller waits while the service provider adds the extra minutes to the bill. Again, the caller is billed more than required.
Service providers can be involved in FAS fraud. But, it can also be the VOIP wholesaler to whom the service provider routes the call.
- PBX Hacking
In PBX Hacking, hackers exploit private telephone networks to make calls at another party’s expense. The “party” is a business that uses the PBX system to make calls at a mass level.
Calls made by hackers are usually long-distance calls that carry higher than average charges. In most cases, businesses do not realize that they’re footing the bill for unauthorized calls.
Hackers try to hide such calls to continue the fraud as long as possible. PBX Hacking is a common form of VOIP fraud. Most businesses are unaware of certain security steps they should take; an example is changing the PBX system’s default password.
Hackers are always on the lookout for insecure PBX systems. Once they figure out the IP address of the insecure PBX system, they attempt to access it to make unauthorized calls.
Addressing Fraud Prevention: Solutions to Combat Telecom Scams
- CDR Analysis
Call Detail Record (CDR) analysis accurately analyzes different VOIP metrics to detect anomalies and mitigate fraud. The process analyzes information available within a Call Detail Record (CDR).
The information available here includes call duration, sender number, latency, unique record identifier, etc. To explain more broadly, this information is enough to assess any unwanted activity that might originate on the network.
Service providers can set criteria to assess what might count as unwanted activity. Factors include incoming-outgoing call ratio, repetitive calls from the same caller ID, numbers within a similar range, etc.
CDR analysis can further be coupled with advanced AI/Data Analytics tools to derive more accurate results. A number of steps should be followed to perform CDR analysis in the context of VOIP fraud. Read our blog to understand this process in more detail.
- Third-Party Routing
In many cases, the service provider might not have the adequate in-house infrastructure to combat VOIP fraud. And if the service provider starts seeing a massive rise in VOIP fraud-related cases, it could spell trouble. The service provider might be unable to bear the cost lost to fraud-related activities.
Third-party routing helps combat this fraud by shifting the responsibility to another operator. Under an agreement between the operators, certain calls flagged for suspicious activity can be routed for validation purposes.
- Call Blocking
Call blocking involves restricting calls from regions where fraudulent activity originates. A service provider opts out of the revenue that might otherwise have come in from the given region. But in many cases, the cost lost to VOIP fraud outweighs the profit.
- Using AI/Data Analytics
AI/Data analytic techniques are ideal for an industry such as the telecom sector. Given the scale and sheer number of users attached to each service provider, it’s safe to say there’s no shortage of data to go around.
Coupling this with a technique such as CDR analysis can generate more accurate and valuable insights. In addition, the service provider can detect anomalies in real-time. AI tools can further be used to quickly respond to any fraudulent activity detected.
How Synaptique uses AI & Data Analytics to Combat Fraud for the Telecom Sector
Some techniques mentioned here such as Call Blocking do work. But, it’s still a ‘hard line’ approach that completely shuts out entire regions from basic telecom facilities. People in the restricted region using the telecom services for ethical practices are deprived of a basic human right.
Other techniques such as CDR analysis do work to some extent. But, the data being gathered is for potentially millions of users. And per user, you’re analyzing several metrics. This is why you need a more sophisticated way of understanding the large amount of data.
Enter Synaptique. We leverage existing techniques such as CDR analysis and couple them with AI/ML models. The result is a hybrid technique that is more effective in mitigating fraudulent activity.
Our S-One Analytics tool quantifies all of this into an easy-to-use platform. To learn more, book a free demo to see firsthand how Synaptique can help you decrease fraud-related losses.
Posted on July 27, 2022 by Yassine, LASRI