Atteindre la maturité en Business Assurance et en gestion de la fraude
Maîtriser les cinq piliers : Organisation, Personnel, Processus, Outils et Influence
La fraude et les pertes de revenus représentent des menaces constantes pour les opérateurs télécoms et les régulateurs, et évoluent au même rythme que les technologies et services. Pour les opérateurs soucieux de sécuriser leurs revenus et protéger l’intégrité de leur activité, une fonction mature de Business Assurance et de gestion de la fraude (BAFM) n’est pas seulement une bonne pratique, c’est une nécessité.
Dans cet article, nous vous présentons les cinq piliers fondamentaux qui doivent être alignés pour développer une fonction BAFM mature et durable : Organisation, Personnel, Processus, Outils et Influence.
Organisation : Structurer pour l’efficacité et l’indépendance
Le premier pas vers la maturité en BAFM est de disposer de la bonne structure organisationnelle. La fonction doit être clairement définie dans l’organigramme de l’entreprise, idéalement opérant de manière indépendante des unités opérationnelles et génératrices de revenus, pour maintenir la neutralité et l’objectivité.
Points clés :
- Établir la BAFM comme département autonome ou l’intégrer à l’audit interne, aux finances ou à la gestion des risques.
- Définir des rôles et responsabilités clairs pour les équipes en charge de la détection de fraude, de l’assurance des revenus et du reporting.
- Garantir un accès direct à la direction pour une meilleure visibilité et influence.
Astuce : L’alignement avec les normes réglementaires ou de gouvernance du groupe renforce la crédibilité et pose les bases d’un déploiement élargi.
Personnel : Développer les compétences et une culture de vigilance
Les ressources humaines sont le moteur d’une fonction BAFM efficace. Même les meilleurs systèmes ne peuvent pas détecter ou empêcher les fraudes sans des professionnels qualifiés et conscients de l’évolution des menaces.
Points clés :
- Recruter ou former des experts en opérations télécom, analyse de données, audit et cybersécurité.
- Promouvoir une culture de responsabilité et de vigilance à tous les niveaux.
- Favoriser l’apprentissage continu et les certifications (ex : CFCA, ACFE).
Astuce : Allier expertises internes et consultants externes pour des perspectives renouvelées et une meilleure capacité d’adaptation.
Processus : Formaliser et standardiser les flux de travail
Des processus bien documentés et reproductibles sont essentiels pour la maturité de la fonction BAFM. Sans procédures opérationnelles standardisées (SOP), même les équipes les plus compétentes peuvent rencontrer des difficultés.
Points clés :
- Documenter les flux de travail pour la détection, l’investigation, l’escalade et la clôture des fraudes.
- Aligner les contrôles d’assurance des revenus sur les principales sources : voix, SMS, data, et mobile money.
- Intégrer les processus BAFM à la gestion des incidents et aux pistes d’audit.
Astuce : Utiliser des indicateurs de performance (KPI) et des journaux d’audit pour mesurer l’efficacité des processus.
Outils : Exploiter l’automatisation et l’intelligence
Le bon système technologique est l’épine dorsale d’une fonction BAFM moderne. Les processus manuels ne peuvent plus suivre le rythme et la complexité des services télécoms actuels.
Points clés :
- Investir dans des outils de surveillance en temps réel, de détection d’anomalies via l’IA et de tableaux de bord personnalisables.
- Assurer l’intégration avec les différentes sources de données : CDRs, facturation, IN, MFS, CRM.
- Automatiser les tâches répétitives : seuils d’utilisation, rapprochement, génération de rapports.
Astuce : Nos solutions S-ONE RA et S-ONE FRAUD sont conçues pour offrir une couverture complète de l’assurance télécom, avec des alertes intelligentes et une détection des fuites de revenus.
Influence : Créer un impact au-delà de l’équipe BAFM
Une fonction BAFM mature exerce une influence au-delà de ses frontières. Elle collabore de manière transversale, obtient le soutien de la direction, et contribue aux décisions stratégiques via l’analyse des données.
Points clés :
- Mettre en place un reporting régulier pour informer les dirigeants des tendances et risques.
- Collaborer avec les départements ventes, marketing, IT et produits pour intégrer la prévention dès la conception.
- Entretenir des relations avec les parties prenantes externes : régulateurs, auditeurs, forums sectoriels.
Astuce : L’influence ne se résume pas à l’autorité, elle repose sur la crédibilité. Des résultats concrets et réguliers renforceront votre légitimité.
En conclusion : La maturité est un parcours, pas une destination
Le développement d’une fonction BAFM ne se fait pas du jour au lendemain. Il s’agit d’une évolution stratégique nécessitant un investissement continu dans les compétences, les processus et la technologie. Mais les bénéfices sont significatifs : augmentation des revenus, réduction des pertes frauduleuses, et renforcement de la confiance des clients et partenaires.
Chez Synaptique, nous accompagnons les opérateurs télécoms dans le renforcement de leurs capacités d’assurance grâce à des outils intelligents, des services experts et des stratégies adaptées.
Achieving Maturity in Business Assurance and Fraud Management
Mastering the Five Pillars: Organization, People, Process, Tools, and Influence
Fraud and revenue leakage are constant threats for telecom operators and regulators that evolve just as quickly as the technology and services we offer. For telecom operators committed to secure their revenues and protect their business integrity, a mature Business Assurance and Fraud Management (BAFM) function is not just a best practice, it’s a necessity.
In this article, we’ll walk you through the five foundational pillars that must be aligned to achieve a truly mature and sustainable BAFM capability: Organization, People, Process, Tools, and Influence.
- Organization: Structuring for Efficiency and Independence
The first step toward maturity in BAFM is having the right organizational structure. A mature function must be clearly defined within the company’s organization chart, ideally operating independently from operational and revenue generating units to maintain neutrality and objectivity.
Key Considerations:
- Establish BAFM as a standalone department or within Internal Audit, Finance, or Risk Management.
- Define clear roles and responsibilities across fraud detection, revenue assurance, and reporting teams.
- Ensure direct access to senior leadership for visibility and influence.
Pro Tip: Alignment with regulatory or group governance standards adds credibility and sets a strong foundation for expansion.
2. People: Building the Right Skills and Culture
People are the engine of a successful BAFM function. Even the best systems can’t detect or prevent fraud without skilled professionals who understand both the business and the evolving threat landscape.
Key Considerations:
- Hire or upskill professionals in telecom operations, data analytics, audit, and cybersecurity.
- Foster a culture of accountability and vigilance across all departments.
- Promote continuous learning and certifications (e.g., CFCA, ACFE) to stay ahead of fraud trends.
Pro Tip: Combine internal experts with external consultants or technology partners for fresh insights and scalability.
- Process: Defining and Standardizing Workflows
Having well-documented, repeatable processes is critical to a mature BAFM function. Without standard operating procedures (SOPs), even skilled teams can falter under pressure.
Key Considerations:
- Document workflows for fraud detection, investigation, escalation, and closure.
- Align revenue assurance checks with key revenue streams: voice, SMS, data, and mobile money.
- Integrate BAFM processes with incident management and audit trails.
Pro Tip: Use KPIs and audit logs to measure process effectiveness and demonstrate value to leadership.
4. Tools: Leveraging Automation and Intelligence
The right technology stack is the backbone of modern BAFM functions. Manual processes can’t scale to handle the volume, speed, and complexity of telecom services today.
Key Considerations:
- Invest in tools that provide real-time monitoring, AI-based anomaly detection, and customizable dashboards.
- Ensure integration across multiple data sources: CDRs, Billing, IN, MFS, and CRM systems.
- Automate repetitive tasks such as usage threshold checks, reconciliation, and report generation.
Pro Tip: Our S-ONE RA and S-ONE FRAUD solutions are purpose-built to provide end-to-end assurance for telecom environments, including intelligent alerting and revenue leakage detection.
- Influence: Driving Change Beyond the BAFM Team
A mature BAFM function extends its influence beyond the boundaries of its own team. It works cross-functionally, gains executive support, and helps shape company-wide decisions through data-driven insights.
Key Considerations:
- Establish regular reporting mechanisms to share trends and risk insights with C-level executives.
- Partner with sales, marketing, product, and IT to embed fraud prevention and assurance early in the service lifecycle.
- Cultivate relationships with external stakeholders like regulators, auditors, and industry forums.
Pro Tip: Influence is not only about authority, it’s about credibility. Consistently delivering results will earn you a seat at the strategy table.
Final Thoughts: Maturity is a Journey, Not a Destination
Maturing your BAFM function doesn’t happen overnight, it’s a strategic evolution that demands investment in people, processes, and technology. But the payoff is significant: stronger revenues, reduced fraud losses, and higher trust from customers and stakeholders.
At Synaptique, we specialize in helping telecom operators level up their assurance capabilities with intelligent tools, expert services, and tailored strategies.
How AI is Transforming Revenue Assurance Systems for Telecom Operators
Smarter, Faster, and More Proactive with S-ONE RA
As margins are thin and services are increasingly complex, revenue assurance (RA) has become a mission-critical function and revenue leakage and fraud continue to pose serious threats to operators’ profitability. Operators are constantly seeking more accurate, efficient, and proactive ways to detect and eliminate revenue leakages across their networks. And today, artificial intelligence (AI) is emerging as the game-changer.
But how exactly is AI transforming revenue assurance systems? What tangible benefits does it offer to RA specialists? And how can telecom operators harness its power to protect every dollar they earn?
Let’s unpack it.
From Reactive to Proactive: Why AI is a Game-Changer for Revenue Assurance
Traditionally, revenue assurance relied heavily on post-event reconciliation and rule-based systems. These systems, while valuable, often reacted to revenue losses after they occurred. Manual audits, static KPIs, and fragmented data sets made it hard to detect issues in real-time, let alone predict them.
AI changes the game. With machine learning algorithms and intelligent data processing, operators can now:
- Analyze massive volumes of transactional and network data in real-time
- Detect anomalies and irregularities as they happen
- Predict potential leakage points before they cause losses
- Automate reconciliation between network, billing, and IN systems
Instead of relying on static rules or periodic audits, AI empowers telecoms operators with systems that adapt to evolving patterns, detect subtle discrepancies, and act faster than ever before.
Key Use Cases: Where AI is Creating Real Value
AI-powered revenue assurance platforms like S-ONE RA by Synaptique are already helping telecom operators secure their revenue in several key areas:
- Intelligent Reconciliation: By leveraging AI, S-ONE RA can reconcile CDRs across the core network (MSC, SGSN/GGSN, SMS-C) and IN in near real-time. This dramatically improves the accuracy of voice, SMS, and data usage billing, preventing discrepancies that often slip through traditional rule-based checks.
- Anomaly Detection: Rather than relying solely on static thresholds, AI models learn from historical data patterns to identify outliers. These could be unexpected usage spikes, mismatched billing entries, or suspicious traffic flows that may indicate configuration errors or fraud.
- Revenue Leakage Prediction: Predictive analytics help identify where future leakage is most likely to occur – whether from faulty provisioning, delayed billing, roaming errors, or even system integration issues.
- Operational Efficiency: AI reduces the need for manual audits by automating routine controls and surfacing only high-priority issues. This allows RA teams to focus on investigation and strategy rather than firefighting.
- Real-Time Fraud Detection and Revenue Protection: One of the biggest advantages of AI in Revenue Assurance Systems is the ability to detect fraudulent behavior in real time. Machine learning models can process vast datasets across services (voice, SMS, data, mobile money), identifying inconsistencies or usage patterns that would go unnoticed by traditional systems.
- Examples of AI-powered detection:
-
- Suspicious call routing patterns
-
- SIM box fraud detection
-
- Unexpected revenue drops or service anomalies
-
- Inconsistent IN vs. MSC vs. billing data
These real-time alerts allow operators to act before damage is done, minimizing losses and increasing customer trust.
- Automation and Predictive Insights: Automation is at the core of an AI-enabled revenue assurance strategy. With AI, operators can streamline repetitive tasks such as:
- Reconciliation of transaction logs, CDRs, and billing records
- Threshold-based alerting
- Root cause analysis for discrepancies
Even more powerful is AI’s predictive capability. These systems can learn from historical patterns to anticipate issues like fraud spikes, system bottlenecks, or revenue dips — enabling proactive resolution before they affect the business.
What RA Specialists Need to Know
Revenue assurance teams often ask:
- Can AI replace traditional audit processes? Not replace, but enhance. AI amplifies your control framework by making it smarter and more responsive.
- Will AI increase our workload? On the contrary. AI streamlines monitoring and triage so you can focus on analysis, not chasing false positives.
- Is implementation complex? With the right platform and partner, deployment can be incremental and non-disruptive.
S-ONE RA: Synaptique’s AI-Powered Revenue Assurance System
At Synaptique, we’ve built S-ONE RA to meet the real-world needs of modern telecom operators. It’s more than a tool — it’s an intelligent, scalable platform designed to bring clarity, control, and confidence to your revenue assurance function.
Key Capabilities of S-ONE RA:
- Real-time reconciliation across network elements
- AI-powered anomaly detection and automated alerting
- Customizable dashboards and KPIs
- End-to-end visibility across voice, data, SMS, and mobile money
- Modular design to adapt to your network and services
If you’re looking to modernize your Revenue Assurance System, Synaptique is here to help. Whether you’re just starting or optimizing a mature RA function, S-ONE RA brings the automation, intelligence, and agility you need to stay ahead.
Download the S-ONE RA brochure to learn more, or Schedule a call with our experts to discuss your revenue assurance strategy.
Final Thoughts: The Future is AI-Assisted
Revenue assurance in telecom is no longer just about plugging leaks, it’s about building resilient, intelligent systems that adapt to evolving risks. AI is not a buzzword here; it’s a fundamental shift in how we protect revenue, ensure service accuracy, and build trust with customers.
In the telecom industry billions of transactions occur every day, so ensuring accurate revenue capture and minimizing leakage is essential. Revenue Assurance (RA) teams play a critical role in this effort, relying heavily on actionable insights derived from data. Dashboards are central to this process, offering RA teams the ability to monitor, analyze, and act on key metrics in real-time. Here, we explore the importance of dashboards in revenue assurance and provide a detailed breakdown of the essential dashboards S-ONE RA offers, the metrics they include, and their importance.
1. Revenue Assurance Dashboard
Metrics Included:
- Total revenue generated (daily, weekly, monthly)
- Revenue breakdown by service (voice, SMS, data, roaming)
- Anomalies in revenue trends
- Comparison of projected vs. actual revenue
Why It’s Needed:
This dashboard provides a bird’s-eye view of revenue streams, allowing RA teams to monitor overall performance and detect irregularities quickly. Identifying revenue declines or unexpected spikes ensures that any underlying issues, such as system misconfigurations or fraudulent activities, are addressed promptly.
2.Data Reconciliation Dashboard
Metrics Included:
- Volume of reconciled vs. unreconciled call detail records (CDRs)
- Data reconciliation success rates
- Discrepancies between network records and billing systems
- Mediation system logs for dropped or rejected records
Why It’s Needed:
Accurate reconciliation of data ensures that all usage is billed correctly. This dashboard helps RA teams identify gaps in data processing, such as missed CDRs, and fix issues before they impact revenue. By highlighting reconciliation discrepancies, the dashboard minimizes revenue leakage.
3. Fraud Detection Dashboard
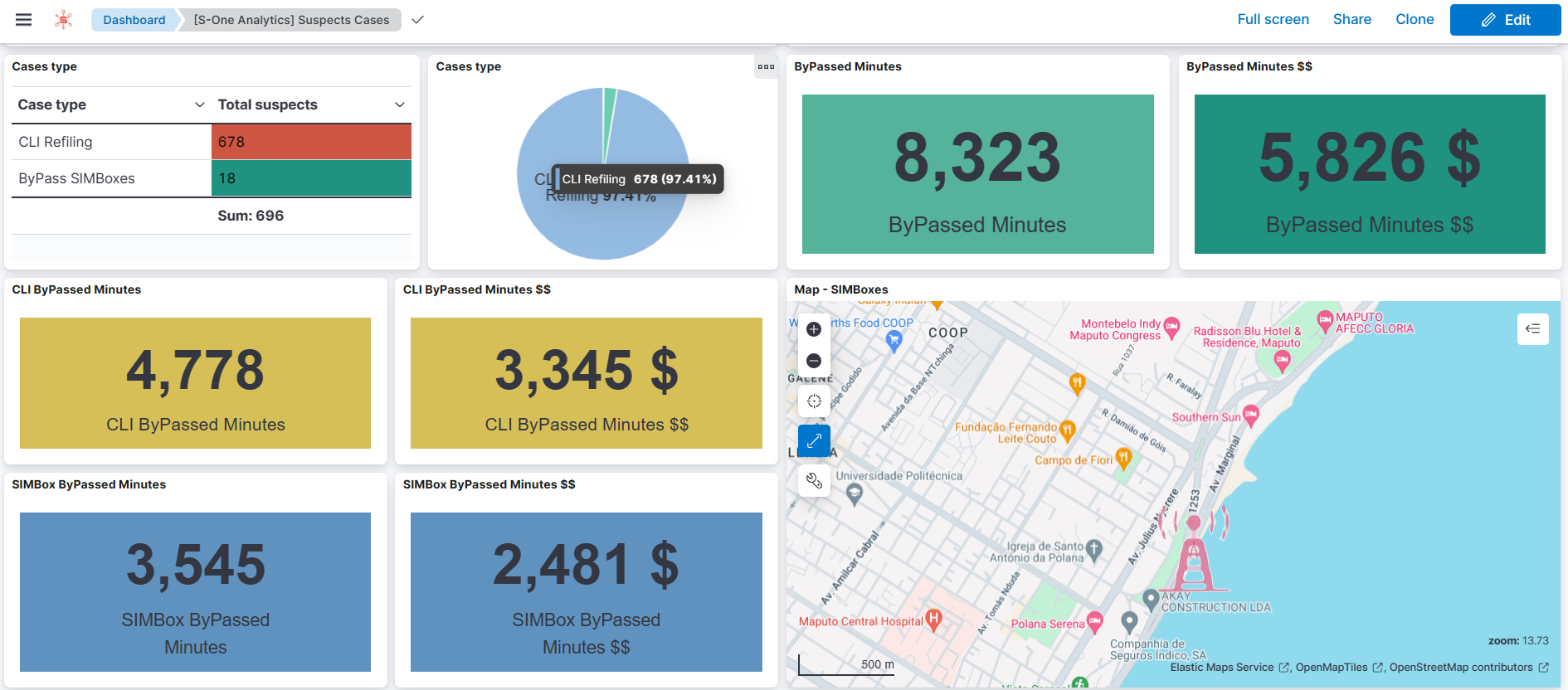
Metrics Included:
- Number of flagged fraud events
- Types of fraud detected (e.g., Simbox bypass,CLI bypass fraud)
- Locations and timestamps of suspicious activities
- Revenue impact of identified fraud
Why It’s Needed:
Fraudulent activities pose significant threats to revenue. This dashboard provides real-time alerts and detailed analyses of fraud patterns, enabling RA teams to take swift action to mitigate risks. It also helps in evaluating the effectiveness of anti-fraud measures over time.
4. Interconnect and Roaming Revenue Dashboard
Metrics Included:
- Revenue from interconnect agreements
- Roaming revenue breakdown by partner and region
- Settlement discrepancies with partner operators
- Trends in interconnect and roaming traffic
Why It’s Needed:
Revenue from interconnect and roaming agreements can be complex to manage. This dashboard ensures accurate tracking and settlement of revenue with partner operators. By identifying discrepancies in real-time, RA teams can avoid disputes and recover potential losses effectively.
5. Customer Complaint Analysis Dashboard
Metrics Included:
- Volume of billing-related complaints
- Average resolution time for disputes
- Financial impact of resolved and unresolved complaints
- Trends in complaint categories
Why It’s Needed:
Customer complaints often highlight gaps in billing accuracy or network performance. This dashboard helps RA teams identify recurring issues, assess their financial impact, and implement measures to improve customer satisfaction and revenue assurance processes.
6. Network Performance Dashboard
Metrics Included:
- Call drop rates and their financial impact
- SMS delivery success rates
- Data session completion rates
- Alerts for network element failures (e.g.,SMS-C, MSC, SGSN, GGSN)
Why It’s Needed:
Technical issues in the network can lead to unbilled usage and lost revenue. This dashboard provides visibility into network performance, allowing RA teams to collaborate with technical departments to resolve issues that impact revenue capture.
How S-ONE RA Delivers Exceptional Dashboards
S-ONE RA, powered by advanced machine learning, offers pre-configured and customizable dashboards tailored to the unique needs of telecom operators. Here’s how it stands out:
Real-Time Data Integration
S-ONE RA seamlessly integrates with mediation systems, billing platforms, and network data sources to provide comprehensive, real-time insights.
AI-Driven Anomaly Detection
Machine learning algorithms continuously analyze data streams to detect and highlight anomalies, enabling proactive resolution of issues.
Customizable Dashboards
Operators can customize dashboards to focus on their specific priorities, such as high-value customers or roaming revenue analysis.
Automated Reporting
Dashboards include automated reporting features that generate summaries for stakeholders, complete with visualizations and actionable recommendations.
Dashboards include automated reporting features that generate summaries for stakeholders, complete with visualizations and actionable recommendations.
Download our S-ONE RA brochure to discover more about the solution to unlock the full potentiel of our dashbords.
For a live demonstration of S-ONE RA’s capabilities, including its powerful dashboards, Book a Call today and see how we can transform your revenue assurance processes.
Conclusion
Dashboards are indispensable tools for revenue assurance teams, offering clarity, control, and actionable insights to safeguard revenue and enhance operational efficiency. With S-ONE RA’s advanced dashboards, telecom operators gain the power to monitor critical metrics, identify revenue leakage, and drive sustainable growth.
For a live demonstration of S-ONE RA’s capabilities, including its powerful dashboards, contact us today and see how we can transform your revenue assurance processes.
Revenue Assurance (RA) and Fraud Management (FM) are critical functions for telecom operators aiming to protect their network, revenue streams and minimize financial losses. Ensuring these teams have access to the right data is essential for identifying discrepancies, addressing vulnerabilities, and implementing robust controls. Below is a detailed guide on the type of data to rovide to RAFM Teams to enhance revenue assurance and prevent revenue leakage effectively.
Type of Data to Provide to RAFM Teams by Telecom operators
1. Call Detail Records (CDRs)
Why They Are Essential: CDRs provide detailed information about every call made or received on the network, including time, duration, source, destination, and cost. RAFM teams use CDRs to identify discrepancies between billed and actual usage.
Key Attributes:
- Call start and end times
- Caller and recipient numbers
- Call type (e.g., local, international, roaming)
- Network element IDs (e.g., MSC,OCS)
- Applied rates and chargesUse Case: Reconciliation of CDRs against billing system data to detect under-billing or over-billing issues.
2. Data Usage Records
Why They Are Essential: Ensuring that all data usage is accurately captured and billed is crucial. Data usage records provide details on internet and app usage patterns by subscribers.
Key Attributes:
- Data session start and end times
- Volume of data transferred (upload/download)
- Session type (e.g., streaming, browsing)
- Associated costs and plans
Use Case: Reconciliation of data session records with charging systems to identify unbilled usage.
3. SMS Records
Why They Are Essential: SMS remain significant revenue sources, particularly in regions with lower internet penetration. RAFM teams need to ensure proper billing for all messaging services.
Key Attributes:
- Sender and recipient numbers
- Message type (e.g., domestic, international, bulk)
- Time of delivery
- Billing rates
Use Case: Cross-verification of SMS records with billing platforms to detect revenue leakage from promotional offers or network issues.
4. Subscriber Information and Profiles
Why They Are Essential: Accurate subscriber data ensures that customers are billed according to their subscribed plans, discounts, and usage patterns.
Key Attributes:
- Customer name and account details
- Subscription type (prepaid/postpaid)
- Plan details (e.g., data caps, call minutes, SMS bundles)
- KYC compliance data
Use Case: Reconciliation of subscription data with billing plans to detect discrepancies like incorrect plan activations or unregistered users.
5. Network Event Logs
Why They Are Essential: Network event logs provide insights into the functioning of core and intelligent network elements. These logs are crucial for identifying technical glitches that may lead to revenue leakage.
Key Attributes:
- Network element activity logs
- Error codes and failure records
- Timestamped records of events
Use Case: Identifying dropped calls or failed SMS deliveries that are not billed despite usage.
6. Billing System Data
Why They Are Essential: RAFM teams need access to billing system data to ensure alignment between what customers are charged and their actual usage.
Key Attributes:
- Billed amounts and invoices
- Applied discounts and promotions
- Payment records
Use Case: Auditing billing data against CDRs and subscription plans to ensure billing accuracy.
7. Mediation System Data
Why They Are Essential: The mediation system acts as the bridge between network-generated data and the billing system. Any discrepancies here can lead to revenue leakage.
Key Attributes:
- Raw data from network elements
- Processed data passed to billing systems
- Rejected or dropped records
Use Case: Reviewing mediation logs to identify lost data records that could impact billing.
8. Fraud Alerts and Patterns
Why They Are Essential: Fraudulent activities can lead to significant revenue losses. RAFM teams need detailed fraud data to identify and mitigate risks promptly.
Key Attributes:
- Detected fraud types (e.g.,Simbox bypass,CLI bypass fraud)
- Location and time of fraud occurrences
- Subscriber details involved in suspicious activities
Use Case: Cross-referencing fraud patterns with network and billing data to detect systemic vulnerabilities.
9. Interconnect and Roaming Data
Why They Are Essential: Revenue from interconnect and roaming services is susceptible to discrepancies due to differing billing systems between operators.
Key Attributes:
- Interconnect call/SMS records
- Roaming agreements and charges
- Reconciliation reports from partner operators
Use Case: Auditing interconnect and roaming data to ensure accurate settlements and prevent disputes.
10. Complaint and Dispute Records
Why They Are Essential: Customer complaints about billing inaccuracies can highlight gaps in the revenue assurance process.
Key Attributes:
- Complaint details
- Resolution steps and timelines
- Financial impact of resolved disputes
Use Case: Using complaint data to identify and address recurring issues in billing and revenue collection processes.
How Sharing the Right Data Ensures Effective Revenue Assurance
Sharing accurate and comprehensive data across departments is crucial for ensuring seamless revenue assurance processes. Here’s how it makes a difference:
Seamless Reconciliation of Records:
- Accurate data sharing ensures that network-generated data (e.g., CDRs, data usage records) aligns with billing and subscriber records.
- Helps RAFM teams identify and resolve discrepancies promptly, reducing delays in revenue collection.
Billing Accuracy and Transparency:
- Comprehensive datasets allow RAFM teams to cross-verify usage records against billing system data.
- Minimizes errors such as over-billing, under-billing, or unbilled usage, improving customer trust and satisfaction.
Enhanced Fraud Detection:
- Sharing data across teams allows for cross-referencing fraud alerts with network activity and billing logs.
- Enables faster identification of patterns, such as SIM fraud or unauthorized usage, and allows immediate mitigation.
Improved Decision-Making:
- Access to shared, accurate data provides RA/FM teams with actionable insights to support strategic decisions.
- Supports proactive measures by identifying trends and anomalies before they escalate into significant issues.
Streamlined Collaboration:
- Fosters collaboration between RAFM, IT, and network teams by providing a unified view of operations.
- Reduces silos and ensures all stakeholders are aligned in revenue assurance efforts.
To empower RAFM teams, our solutions S-ONE RA and S-ONE FRAUD provide comprehensive dashboards and analytics tailored to monitor, reconcile, and act on key operational data.
S-ONE RA delivers real-time revenue assurance analytics through customizable dashboards and automated reporting. With features such as detailed call detail records (CDRs) analysis, data usage monitoring, and billing system reconciliation, S-ONE RA enables teams to swiftly identify discrepancies and prevent revenue leakage.
S-ONE FRAUD focuses on fraud monitoring, offering robust analytics to detect and analyze irregular patterns in transaction data. By highlighting suspicious activities—such as potential Simbox fraud, Wangiri, CLI bypass, and other anomalies—S-ONE FRAUD equips RAFM teams with the insights needed to secure the network and protect revenue.
Together, these solutions streamline data sharing across departments and support proactive decision-making. They ensure RAFM teams have a unified view of critical data, enhancing collaboration and operational efficiency.
For more information, download our brochures:
Download S-ONE RA Brochure
Download S-ONE FRAUD Brochure
For a live demonstration of S-ONE RA’s capabilities, including its powerful dashboards, Book a Call today and see how we can transform your revenue assurance processes.
Conclusion
Providing RAFM teams with comprehensive and accurate data is the foundation for effective revenue assurance and fraud prevention. By ensuring access to CDRs, data usage records, subscriber profiles, and other key datasets, telecom operators can proactively identify and resolve revenue leakage issues. Moreover, fostering collaboration between network, IT, and RAFM teams can further strengthen controls and enhance financial performance.
To succeed in this mission, operators must also invest in advanced analytics tools and automated reconciliation systems to process and analyze data efficiently. Revenue assurance is not just about preventing losses but also about building a robust framework that ensures long-term profitability and customer trust.
Telecom operators face constant challenges in ensuring accurate reconciliation between core and intelligent network elements for preventing revenue leakage and ensuring seamless service delivery. During our recent webinar, Preventing Revenue Leakage: Core vs. Intelligent Network Reconciliation, we explored:
- The importance of reconciling data between core network elements (MSC, SMS-C, GGSN, SGSN) for revenue assurance.
- Common challenges encountered in Voice, SMS, and Data reconciliation.
- Practical demonstrations on reconciling data effectively between core network elements and the Intelligent Network (IN) to prevent revenue leakage and ensure data accuracy.

We also engaged in a vibrant Q&A session, addressing critical questions from participants. Here’s a recap of the key questions and our expert responses:
1. Why Don’t Postpaid Accounts Show on OCS in MSC vs OCS Reconciliation?
Answer: There are two scenarios:
- OCS manages both prepaid and postpaid accounts: In this case, OCS generates Call Detail Records (CDRs) for all accounts (prepaid, hybrid, postpaid), and these CDRs are reconciled with MSC data.
- OCS manages only prepaid and hybrid accounts: In this scenario, OCS doesn’t generate CDRs for postpaid accounts. Instead, another system (Offline Billing) collects postpaid CDRs directly from MSC for rating. The reconciliation process must include these rated records from Offline Billing to complete the reconciliation.
2. How to Handle Pay-As-You-Go (PAYG) and Bundles for Prepaid Accounts?
Answer: Prepaid subscribers their voice, SMS, and data usage can be charged as follows:
- PAYG (Pay-As-You-Go) charges are deducted from the main account for airtime.
- Free resources purchased via main account airtime or mobile money wallet.
For both scenarios the reconciliation process traces the sms, voice and data usages in both MSC and OCS. However, reconciling free resource usage vs. bundle purchased at the OCS level accuracy depends on how operators manage balances:
- If operators use separate balances for each bundle, the reconciliation process is straightforward and can verify the accuracy of the consumption of the bundle.
- If operators accumulate free resources from different bundles into a single balance, reconciliation becomes more complex.
3. How Do You Manage Different Operator File Structures in CDR Analysis Tools (e.g., Ericsson vs Huawei)?
Answer: The reconciliation process is designed to be scalable and vendor-agnostic. All vendor CDRs are mapped into a unified schema, ensuring compatibility and streamlined analysis across different systems.
4. How Can VoLTE Reconciliation Be Effectively Done?
Answer: VoLTE reconciliation involves challenges related to both voice and data portions of traffic. While a deep dive into this topic is planned for a dedicated webinar, initial considerations include correlating VoLTE data and voice records across network elements and billing systems.
5.Est-il possible d’identifier les numéros qui peuvent émettre des appels mais pas identifiés sur IN (ENG:Is It Possible to Identify Numbers That Can Make Calls but Are Not Registered on the IN?
Answer: Yes, it is possible. The reconciliation process must access Know Your Customer (KYC) data from CRM to enrich CDRs from both MSC and OCS. This enables filtering for non-identified subscribers engaging in traffic (voice, SMS, or data).
6. Comment détecter des numéros créés sur HLR et non sur IN (ENG:How Can We Detect Numbers Created on HLR but Not on IN?)
Answer: This can be achieved by reconciling dumps from HLR and OCS. By comparing these datasets, it’s possible to identify MSISDNs enabled on the HLR but not on the OCS.
7.Please can you guide us on how to effectively reconcile PGW vs OCS
Answer: The PGW usually generates a lot of intermediate CDRs with a unique correlation ID called the Charging ID, which is also reported in data charging CDRs from OCS. Effective reconciliation involves:
- Aggregating CDRs from PGW.
- Joining aggregated data with OCS records using MSISDN and Charging ID.
Key Takeaways from the Webinar
- Data reconciliation is essential for ensuring revenue assurance and preventing revenue leakage.
- Challenges vary across network elements, but scalable, vendor-agnostic solutions simplify the process.
- Accurate reconciliation requires enriching datasets with external information like KYC data.
- Collaboration between network teams and revenue assurance specialists is crucial for success.
Access the Webinar Recording
Missed the webinar or want to revisit specific sections? Watch the full recording for detailed insights and practical demonstrations:
📺 Watch the Webinar Recording Now
If you have further questions or need personalized support for your reconciliation challenges, don’t hesitate to reach out to our team. Let’s work together to safeguard your revenue and optimize your operations!
Upcoming Events
- All
- Webinar
- Conference
- Expo
novembre 13, 2024
Webinar Preventing Revenue Leakage Core vs. Intelligent Network Reconciliation
join us for an insightful live session on " Core…
Read Moreseptembre 14, 2024
Synaptique at GITEX GLOBAL 2024
Join our team at GITEX Global from October 18 to 24,…
Read Moreseptembre 5, 2024
Synaptique at TARS Africa 2024 in Casablanca 12-13 September
Join us at TARS Africa 2024 in Casablanca 12-13 September,…
Read More