How Telecom Operators Can Fight Wangiri Fraud with AI and Machine Learning
One of the most persistent and insidious forms of telecom fraud is Wangiri fraud, a term that comes from the Japanese phrase meaning “one ring and cut.” This scam has proven incredibly difficult to eliminate using traditional defenses. But with the rise of Artificial Intelligence (AI) and Machine Learning (ML), telecom operators now have powerful tools to outsmart these fraudsters.
Why Traditional Fraud Detection Falls Short
Legacy fraud systems typically rely on fixed rules and thresholds (e.g. blocking all calls to certain prefixes or flagging any call shorter than a few seconds). Such static filters become obsolete as scammers evolve their behavior, and they often generate many “false positives” – legitimate calls wrongly blocked – frustrating users. By contrast, AI/ML approaches do not require manually coded patterns. They ingest massive Call Detail Records (CDRs) and usage data to learn what normal calling behavior looks like, then flag only statistically anomalous events. In practice, telecoms are moving to these techniques: for instance, operators now “monitor call patterns at scale” using machine learning and analytics, automatically blocking calls or numbers “linked to Wangiri scams”. This shift from reactive, rule‑based screening to adaptive data-driven detection is crucial because fraudsters continuously find new loopholes that static systems miss.
How AI and Machine Learning Can Combat Wangiri Fraud
AI and ML technologies are changing the game, allowing telecom operators to move from reactive defenses to proactive and predictive fraud prevention. By analyzing massive volumes of call data and identifying hidden patterns, these technologies offer unprecedented accuracy and speed in detecting Wangiri and other telecom fraud schemes.
AI and ML enable a proactive, multi-faceted defense. In particular, telecoms can leverage these techniques:
Anomaly and Behavioral Detection:
Machine learning models first establish dynamic baselines of normal call behavior (by region, subscriber, time of day, call duration, frequency, etc.). Sophisticated models (neural nets, clustering algorithms, autoencoders, etc.) then identify outliers – for example, a sudden spike of very short international calls from one account, that deviate sharply from the norm. Such unsupervised or semi-supervised methods can flag suspicious patterns that static rules would miss. For example, clustering algorithms group subscribers by similar usage and automatically highlight any individual whose call profile is anomalous. Over time the model adapts: it can learn new fraud patterns as they emerge, so its detection acuity improves continuously
Predictive Risk Scoring:
Beyond spotting active attacks, AI enables predictive analytics, forecasting which calls or accounts are likely to involve fraud. Models are trained on historical fraud incidents (often including confirmed Wangiri cases) along with real-time indicators (e.g. sudden changes in calling patterns). Each incoming call or subscriber account can be assigned a fraud risk score based on features like unusual call targets or timing. High-risk calls can then be automatically blocked or routed for human review before any billing occurs. This lets operators “anticipate fraud before it happens”, effectively neutralizing scams early. In practice, AI-driven scoring often integrates multiple signals (e.g. mismatched calling behavior combined with a known suspicious number prefix) to sharply improve prediction accuracy. By acting on these risk scores (e.g. invoking additional verification or temporarily suspending a call), operators can stop many Wangiri callbacks and revenue shares before victims are charged.
Real-Time Monitoring and Response:
Speed is critical in Wangiri schemes. AI/ML systems can process live call streams and CDR feeds in real time, unlike older systems that batch‑process logs with delays. This means suspicious one-ring calls are flagged and blocked on the fly. For example, advanced platforms issue immediate alerts when unusual call patterns emerge, enabling operators to swiftly cut off fraud attempts. Real-time analytics also allow instant customer notifications or interactive challenges (e.g. sending a warning SMS before connecting a high-risk callback). Reducing the window of exposure effectively shrinks the fraudsters’ opportunity.
Continuous Learning and Adaptation (Adaptive Learning and Model Updating):
Underlying all of the above is the fact that AI/ML systems can continuously update themselves. Unlike static rule engines, modern fraud detection models retrain regularly on new call data. For example, reinforcement learning or incremental training can automatically incorporate confirmed fraud cases and false alarms, so that the model evolves as scammers change tactics. This means the system’s notion of “normal” behavior is always current. As a result, even novel Wangiri variants (e.g. “Wangiri 2.0” where callbacks are generated by bots) can be detected by learning from emerging data. In sum, a true AI-based fraud platform is not a one-time solution but an adaptive engine: it continually refines its algorithms to stay ahead of fraudsters.
Ensemble Modeling and Behavioral Analytics:
Ensemble models combine multiple machine learning algorithms (e.g., decision trees, neural networks, clustering models) to improve detection accuracy and stability. These models leverage the strengths of different approaches, reducing the likelihood of missed fraud or false positives. Behavioral analytics further enhance fraud detection by examining long-term subscriber usage patterns. Rather than analyzing individual calls in isolation, the system monitors usage trends over time, identifying complex fraud scenarios that may only become apparent through longitudinal analysis.
Each of these strategies , anomaly detection, predictive scoring, real-time response, and iterative learning, works together to create a robust defense. In practice, operators also layer these AI techniques with traditional checks (e.g. blacklists, industry intelligence sharing) for multi-layered security. But AI is the core enabler that boosts accuracy and speed while reducing false positives, addressing the very shortcomings of legacy approaches.
Benefits Enabled by AI/ML:
Early Detection of Emerging Threats
AI models excel at detecting new, previously unseen fraud patterns before they can cause widespread damage. By monitoring deviations from normal behavior, even when no prior rule exists for a particular fraud variant, AI helps telecom operators stay ahead of constantly evolving Wangiri tactics. This shortens the time between the emergence of a new fraud strategy and its effective detection, minimizing losses and customer harm.
Real-Time Fraud Prevention
Real-time monitoring allows telecoms to block or flag fraudulent calls as they occur, rather than responding after financial damage has been done. Calls identified as high-risk can be stopped before they are connected, accounts can be suspended pending investigation, and customers can be proactively notified. This immediate response capability significantly reduces revenue leakage, customer complaints, and reputational damage.
Reduction in False Positives
A key benefit of AI/ML is sharper discrimination between fraud and normal behavior, which significantly cuts down false positives. High false-positive rates (incorrectly blocking legitimate calls) are costly – they irritate customers and waste investigative effort. Machine learning mitigates this by continuously refining its detection models on labeled call data. The system learns to recognize subtle differences between benign anomalies (e.g. someone on vacation making many brief calls) and actual fraud patterns. In practice, this involves techniques like ensemble models (combining multiple classifiers) and behavioral analytics to validate alerts.This careful calibration is crucial: telecoms must block Wangiri scams aggressively, yet avoid “overly aggressive blocking” that harms innocent subscribers. By tuning thresholds, incorporating feedback loops, and leveraging rich feature sets, AI-driven systems strike a balance – catching more fraud while minimizing collateral damage.
Continuous Adaptation to Evolving Fraud Tactics
As scammers continuously change their strategies, static rule-based defenses struggle to keep pace. AI models adapt automatically to new tactics without requiring constant manual updates from fraud teams. By learning from both successful fraud attempts and false alarms, AI systems stay agile, identifying new Wangiri schemes, including sophisticated variants like bot-generated callbacks, as they arise.
Operational Scalability
AI-powered fraud detection systems are built to scale with telecom networks. As subscriber bases grow and call volumes increase, these models can process massive datasets without requiring linear increases in staffing or processing resources. AI/ML solutions allow telecoms to monitor millions of calls per day with consistent accuracy, ensuring both efficiency and cost-effectiveness at scale.
Conclusion: A Smarter Future for Fraud Prevention
Wangiri fraud is a persistent and evolving threat to telecom operators and subscribers alike. Static, rule-based defenses are no longer sufficient , they miss sophisticated scams and can cause collateral damage by blocking legitimate calls. However, AI and machine learning offer a proactive, adaptive, and precise solution. By continuously learning call behaviors, scoring risk in advance, and acting instantly on anomalies, AI-driven systems detect Wangiri schemes far more accurately than older methods. Critically, these systems also minimize false positives, preserving customer trust, protecting revenue and preserving customer trust, and ensure the long-term integrity of operator networks.
Understanding Wangiri Scams: Unveiling the Tactics Impact, Mechanics, and Protection Strategies
Wangiri scams, also known as one-ring scams, continue to plague telecom operators worldwide. These fraudulent schemes may appear simple in execution, but their financial and reputational impact on both operators and subscribers is significant. As fraudsters become more sophisticated, it is crucial for telecom operators to understand how Wangiri scams work and what tools are available to detect and prevent them in real-time.
What is Wangiri Fraud?
“Wangiri” is a Japanese term meaning “one ring and cut.” In telecom Wangiri fraud works by exploiting human curiosity and concern. Fraudsters place brief, unsolicited calls to unsuspecting individuals, letting the phone ring once before hanging up. The missed call is designed to lure the recipient into calling back, often to a premium-rate international number controlled by fraudsters, generating illicit revenue from unsuspecting users.
The simplicity of the Wangiri scheme is what makes it so effective and widespread. Each year, telecom operators lose billions of dollars to this type of fraud. Beyond the financial losses, Wangiri attacks erode customer trust and can damage an operator’s reputation.
To learn more about premium-rate numbers and deepen your understanding of Wangiri fraud, watch our latest webinar titled “Wangiri Scams: How Data Monitoring Can Stop Real Losses from One-Ring Fraud.”
https://www.youtube.com/watch?v=qj5rrnnZzIw&pp=ygUGcmVndWx4
Mechanics of the Scam
- Mass Calling Campaigns: Fraudsters use automated systems to initiate thousands of short-duration calls.
- Triggering Curiosity or Alarm: Calls may come from unfamiliar or international numbers, raising curiosity or concern.
- Callback Trap: When the user returns the call, they are connected to a premium-rate line, often with long hold times or confusing audio loops designed to extend call duration.
- Revenue Generation: Every second the call continues adds profit for the fraudsters, with costs borne by the subscriber or operator.
Impact on Telecom Operators
- Revenue Losses: Wangiri fraud can lead to considerable revenue losses, especially when telecom operators are contractually obligated to absorb call-back charges or reimburse affected customers. Additionally, network congestion from fraudulent call bursts can impact legitimate traffic, reducing overall service efficiency.
- Customer Complaints: Victims of Wangiri scams often lodge complaints, which can strain customer support resources and affect Net Promoter Scores (NPS). Poor customer experiences can lead to churn, particularly in competitive markets.
- Reputational Damage: Repeated or large-scale fraud incidents can damage the brand image, signaling to the public that the operator lacks robust fraud prevention mechanisms. This perception can deter new customer acquisition and erode existing loyalty.
- Regulatory Pressure: Regulators may impose stricter compliance requirements or fines on operators who fail to adequately detect and mitigate telecom fraud. In some regions, operators are required to report fraud trends and implement specific countermeasures.
Strategies for Detection and Prevention
To effectively mitigate Wangiri scams, telecom operators must adopt a proactive and data-driven approach that includes:
- Real-Time Monitoring: Continuously analyze call detail records (CDRs) to detect patterns consistent with Wangiri fraud, such as frequent short-duration calls from specific international codes.
- Traffic Profiling: Leverage historical and real-time data to build behavior-based risk profiles for suspicious numbers, ranges, and call origins. Include metrics like average call duration, return call frequency, and time-of-day activity.
- Automated Alerting: Implement rule-based and AI-driven alerts that notify fraud analysts of anomalies such as sudden spikes in short calls or callbacks to premium-rate numbers, enabling timely intervention.
- Subscriber Education: Proactively inform users through SMS alerts, USSD pop-ups, or social media campaigns about the risks of calling back missed international numbers. Empowering users with awareness significantly reduces fraud success rates.
- Collaboration: Create or participate in industry-wide fraud intelligence networks that facilitate the exchange of blacklisted numbers, fraud trends, and prevention techniques. Unified action increases visibility and speeds up detection across borders.
Introducing the S-ONE FRAUD Wangiri monitoring system
At Synaptique, we understand the operational challenges telecom operators face in combating Wangiri fraud. That’s why we developed the S-ONE FRAUD Wangiri, a solution designed to offer real-time visibility, actionable alerts, and advanced analytics for combatting one-ring scams.
Key Features:
- Real-Time Traffic Surveillance: Monitor call traffic patterns across the network to detect Wangiri campaigns as they unfold.
- Machine learning-Powered Anomaly Detection: Identify deviations from normal traffic behavior using machine learning.
- Intuitive Dashboards: Visualize fraud attempts, trends, and metrics to support rapid decision-making.
- Customizable Alert Rules: Configure alert thresholds to match operator-specific risk appetite and fraud history.
With S-ONE FRAUD, telecom operators gain a critical line of defense against Wangiri fraud, preserving both revenue and customer trust.
To learn more about how S-ONE FRAUD can strengthen your fraud management strategy, download the solution’s brochure and contact our team to schedule a call today.
Conclusion
Wangiri scams may be silent attacks, but their consequences are loud. Understanding the mechanics and impact is the first step toward fighting back. By adopting intelligent, automated solutions like S-ONE FRAUD, telecom operators can move from reactive mitigation to proactive fraud prevention, ultimately reinforcing their role as trusted service providers in a rapidly evolving threat landscape.
Atteindre la maturité en Business Assurance et en gestion de la fraude
Maîtriser les cinq piliers : Organisation, Personnel, Processus, Outils et Influence
La fraude et les pertes de revenus représentent des menaces constantes pour les opérateurs télécoms et les régulateurs, et évoluent au même rythme que les technologies et services. Pour les opérateurs soucieux de sécuriser leurs revenus et protéger l’intégrité de leur activité, une fonction mature de Business Assurance et de gestion de la fraude (BAFM) n’est pas seulement une bonne pratique, c’est une nécessité.
Dans cet article, nous vous présentons les cinq piliers fondamentaux qui doivent être alignés pour développer une fonction BAFM mature et durable : Organisation, Personnel, Processus, Outils et Influence.
Organisation : Structurer pour l’efficacité et l’indépendance
Le premier pas vers la maturité en BAFM est de disposer de la bonne structure organisationnelle. La fonction doit être clairement définie dans l’organigramme de l’entreprise, idéalement opérant de manière indépendante des unités opérationnelles et génératrices de revenus, pour maintenir la neutralité et l’objectivité.
Points clés :
- Établir la BAFM comme département autonome ou l’intégrer à l’audit interne, aux finances ou à la gestion des risques.
- Définir des rôles et responsabilités clairs pour les équipes en charge de la détection de fraude, de l’assurance des revenus et du reporting.
- Garantir un accès direct à la direction pour une meilleure visibilité et influence.
Astuce : L’alignement avec les normes réglementaires ou de gouvernance du groupe renforce la crédibilité et pose les bases d’un déploiement élargi.
Personnel : Développer les compétences et une culture de vigilance
Les ressources humaines sont le moteur d’une fonction BAFM efficace. Même les meilleurs systèmes ne peuvent pas détecter ou empêcher les fraudes sans des professionnels qualifiés et conscients de l’évolution des menaces.
Points clés :
- Recruter ou former des experts en opérations télécom, analyse de données, audit et cybersécurité.
- Promouvoir une culture de responsabilité et de vigilance à tous les niveaux.
- Favoriser l’apprentissage continu et les certifications (ex : CFCA, ACFE).
Astuce : Allier expertises internes et consultants externes pour des perspectives renouvelées et une meilleure capacité d’adaptation.
Processus : Formaliser et standardiser les flux de travail
Des processus bien documentés et reproductibles sont essentiels pour la maturité de la fonction BAFM. Sans procédures opérationnelles standardisées (SOP), même les équipes les plus compétentes peuvent rencontrer des difficultés.
Points clés :
- Documenter les flux de travail pour la détection, l’investigation, l’escalade et la clôture des fraudes.
- Aligner les contrôles d’assurance des revenus sur les principales sources : voix, SMS, data, et mobile money.
- Intégrer les processus BAFM à la gestion des incidents et aux pistes d’audit.
Astuce : Utiliser des indicateurs de performance (KPI) et des journaux d’audit pour mesurer l’efficacité des processus.
Outils : Exploiter l’automatisation et l’intelligence
Le bon système technologique est l’épine dorsale d’une fonction BAFM moderne. Les processus manuels ne peuvent plus suivre le rythme et la complexité des services télécoms actuels.
Points clés :
- Investir dans des outils de surveillance en temps réel, de détection d’anomalies via l’IA et de tableaux de bord personnalisables.
- Assurer l’intégration avec les différentes sources de données : CDRs, facturation, IN, MFS, CRM.
- Automatiser les tâches répétitives : seuils d’utilisation, rapprochement, génération de rapports.
Astuce : Nos solutions S-ONE RA et S-ONE FRAUD sont conçues pour offrir une couverture complète de l’assurance télécom, avec des alertes intelligentes et une détection des fuites de revenus.
Influence : Créer un impact au-delà de l’équipe BAFM
Une fonction BAFM mature exerce une influence au-delà de ses frontières. Elle collabore de manière transversale, obtient le soutien de la direction, et contribue aux décisions stratégiques via l’analyse des données.
Points clés :
- Mettre en place un reporting régulier pour informer les dirigeants des tendances et risques.
- Collaborer avec les départements ventes, marketing, IT et produits pour intégrer la prévention dès la conception.
- Entretenir des relations avec les parties prenantes externes : régulateurs, auditeurs, forums sectoriels.
Astuce : L’influence ne se résume pas à l’autorité, elle repose sur la crédibilité. Des résultats concrets et réguliers renforceront votre légitimité.
En conclusion : La maturité est un parcours, pas une destination
Le développement d’une fonction BAFM ne se fait pas du jour au lendemain. Il s’agit d’une évolution stratégique nécessitant un investissement continu dans les compétences, les processus et la technologie. Mais les bénéfices sont significatifs : augmentation des revenus, réduction des pertes frauduleuses, et renforcement de la confiance des clients et partenaires.
Chez Synaptique, nous accompagnons les opérateurs télécoms dans le renforcement de leurs capacités d’assurance grâce à des outils intelligents, des services experts et des stratégies adaptées.
Achieving Maturity in Business Assurance and Fraud Management
Mastering the Five Pillars: Organization, People, Process, Tools, and Influence
Fraud and revenue leakage are constant threats for telecom operators and regulators that evolve just as quickly as the technology and services we offer. For telecom operators committed to secure their revenues and protect their business integrity, a mature Business Assurance and Fraud Management (BAFM) function is not just a best practice, it’s a necessity.
In this article, we’ll walk you through the five foundational pillars that must be aligned to achieve a truly mature and sustainable BAFM capability: Organization, People, Process, Tools, and Influence.
- Organization: Structuring for Efficiency and Independence
The first step toward maturity in BAFM is having the right organizational structure. A mature function must be clearly defined within the company’s organization chart, ideally operating independently from operational and revenue generating units to maintain neutrality and objectivity.
Key Considerations:
- Establish BAFM as a standalone department or within Internal Audit, Finance, or Risk Management.
- Define clear roles and responsibilities across fraud detection, revenue assurance, and reporting teams.
- Ensure direct access to senior leadership for visibility and influence.
Pro Tip: Alignment with regulatory or group governance standards adds credibility and sets a strong foundation for expansion.
2. People: Building the Right Skills and Culture
People are the engine of a successful BAFM function. Even the best systems can’t detect or prevent fraud without skilled professionals who understand both the business and the evolving threat landscape.
Key Considerations:
- Hire or upskill professionals in telecom operations, data analytics, audit, and cybersecurity.
- Foster a culture of accountability and vigilance across all departments.
- Promote continuous learning and certifications (e.g., CFCA, ACFE) to stay ahead of fraud trends.
Pro Tip: Combine internal experts with external consultants or technology partners for fresh insights and scalability.
- Process: Defining and Standardizing Workflows
Having well-documented, repeatable processes is critical to a mature BAFM function. Without standard operating procedures (SOPs), even skilled teams can falter under pressure.
Key Considerations:
- Document workflows for fraud detection, investigation, escalation, and closure.
- Align revenue assurance checks with key revenue streams: voice, SMS, data, and mobile money.
- Integrate BAFM processes with incident management and audit trails.
Pro Tip: Use KPIs and audit logs to measure process effectiveness and demonstrate value to leadership.
4. Tools: Leveraging Automation and Intelligence
The right technology stack is the backbone of modern BAFM functions. Manual processes can’t scale to handle the volume, speed, and complexity of telecom services today.
Key Considerations:
- Invest in tools that provide real-time monitoring, AI-based anomaly detection, and customizable dashboards.
- Ensure integration across multiple data sources: CDRs, Billing, IN, MFS, and CRM systems.
- Automate repetitive tasks such as usage threshold checks, reconciliation, and report generation.
Pro Tip: Our S-ONE RA and S-ONE FRAUD solutions are purpose-built to provide end-to-end assurance for telecom environments, including intelligent alerting and revenue leakage detection.
- Influence: Driving Change Beyond the BAFM Team
A mature BAFM function extends its influence beyond the boundaries of its own team. It works cross-functionally, gains executive support, and helps shape company-wide decisions through data-driven insights.
Key Considerations:
- Establish regular reporting mechanisms to share trends and risk insights with C-level executives.
- Partner with sales, marketing, product, and IT to embed fraud prevention and assurance early in the service lifecycle.
- Cultivate relationships with external stakeholders like regulators, auditors, and industry forums.
Pro Tip: Influence is not only about authority, it’s about credibility. Consistently delivering results will earn you a seat at the strategy table.
Final Thoughts: Maturity is a Journey, Not a Destination
Maturing your BAFM function doesn’t happen overnight, it’s a strategic evolution that demands investment in people, processes, and technology. But the payoff is significant: stronger revenues, reduced fraud losses, and higher trust from customers and stakeholders.
At Synaptique, we specialize in helping telecom operators level up their assurance capabilities with intelligent tools, expert services, and tailored strategies.
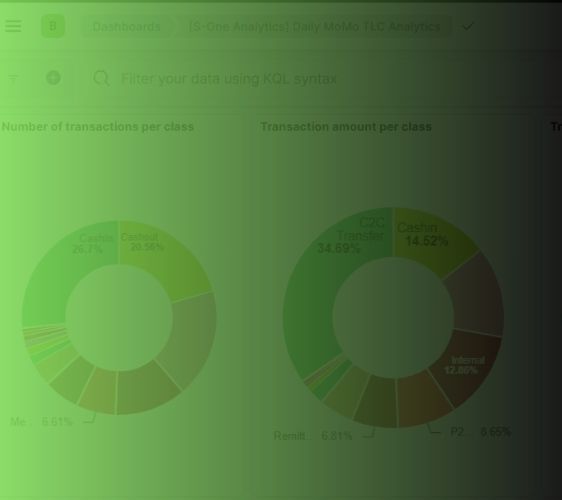
What KPIs and Dashboards Can You Expect from a Mobile Money Transactions Monitoring Solution like S-ONE MFS?
With the rapid rise of Mobile Money services, telecom operators must ensure the integrity, performance, and reliability of mobile transactions. In this context, a dedicated monitoring solution for mobile financial transactions is essential to quickly detect anomalies and optimize revenue. Discover how S-ONE MFS, Synaptique’s Mobile Financial Services monitoring platform, provides dashboards and key performance indicators (KPIs) that help operations, finance, and commercial teams make faster, more informed decisions.
What is S-ONE MFS and How Can It Support Mobile Money Monitoring?
S-ONE MFS is Synaptique’s advanced Mobile Financial Services (MFS) monitoring solution designed for telecom operators. With the rapid rise of mobile money usage across emerging and mature markets, ensuring the integrity, performance, and reliability of mobile money transactions is a growing necessity.
S-ONE MFS provides real-time and historical data visualization, empowering telecom operators with actionable insights across mobile money activities, including peer-to-peer transfers, bill payments, airtime top-ups, merchant transactions, and more.
While S-ONE MFS focuses on operational performance and transaction intelligence, it does not include anti-money laundering (AML) or counter-terrorism financing (CTF) functionalities. Instead, it serves as a powerful observability tool, offering robust analytics, automated alerts, and business intelligence dashboards for revenue assurance and service optimization.
For a complete overview of the features and benefits, you can:
- Download the Brochure
- Book a Call with our team to see the platform in action
What KPIs Can S-ONE MFS Track?
S-ONE MFS provides a rich set of Key Performance Indicators (KPIs) that give telecom operators granular visibility into their mobile money services. Here are the core KPIs the platform can monitor:
Total Transactions
- Tracks the number of transactions processed within specific intervals (daily, weekly, monthly).
- Helps quantify service usage and growth trends.
Transaction Success Rate
- Measures the percentage of successful transactions compared to those that fail.
- Useful for identifying service reliability and technical issues.
Average Transaction Value
- Calculates the average value of all completed transactions.
- Offers insight into user spending behaviors and service value.
Transaction Volume by Channel
- Breaks down transaction data by access channel (e.g., mobile app, USSD, SMS).
- Reveals user preferences and highlights underperforming channels.
Processing Time
- Monitors the average duration for transaction processing.
- Identifies bottlenecks and areas requiring performance optimization.
Error/Failure Rates
- Reports on the frequency of failed transactions caused by system errors or technical issues.
- Crucial for proactive incident management.
User Activity Metrics
- Tracks usage frequency, average transactions per user, and wallet activity.
- Supports customer engagement analysis and service optimization.
Alert Counts
- Monitors the number of system-generated alerts due to anomalies or outliers in transactional behavior.
- Enables rapid response to irregular patterns.
System Availability / Uptime
- Measures platform uptime to ensure reliability and consistent user access.
- Integral for SLA compliance and user satisfaction.
How Are Dashboards Structured in S-ONE MFS?
The dashboards in S-ONE MFS are fully customizable and built using intuitive data visualization tools. They are designed for different operational teams including network operations, finance, and customer service. Dashboards include:
- Operational Monitoring Dashboards
- Live views of transaction counts and success rates
- Alerts for service degradation or outages
- Revenue Insights Dashboards
- Visual breakdown of revenue per service type
- Profitability of agent networks
- Usage & Adoption Dashboards
- Geographic spread of mobile money usage
- Service adoption rates per user segment
- Anomaly Detection Dashboards
- Heatmaps and graphs showing abnormal patterns
- Filters to investigate specific MSISDNs, transaction types, or service periods
How Does S-ONE MFS Help Telecom Operators Make Faster, Smarter Decisions?
S-ONE MFS provides:
- Real-time alerts on transaction failures or volume spikes
- Historical analysis to identify trends and performance issues over time
- Segmented insights to tailor service offerings by user behavior or region
- Exportable reports for management, technical teams, or external partners
This actionable intelligence allows telecom operators to:
- Ensure higher uptime and service continuity
- Improve customer experience by identifying issues quickly
- Optimize agent network coverage and liquidity
- Understand user behavior and introduce new services strategically
Why Is S-ONE MFS a Strategic Tool for Telecom Operators?
Unlike banking-centric monitoring tools, S-ONE MFS is developed with telecom operators in mind. It integrates seamlessly with mobile network systems and provides:
- Minimal deployment time with flexible APIs
- Scalability to match transaction growth
- Telecom-grade security and data management
Moreover, operators can prioritize customer experience and revenue tracking without navigating complex regulatory compliance requirements tied to AML or CTF tools.
Want to See S-ONE MFS in Action?
Our team is happy to show you how S-ONE MFS can be tailored to your needs:
- [Download the Brochure] for an in-depth view of features
- [Book a Call] to schedule a personalized demo with one of our experts
Make mobile money monitoring smarter, faster, and operator-focused with S-ONE MFS.
Avec l’essor fulgurant des services de Mobile Money, les opérateurs télécoms doivent garantir l’intégrité, la performance et la fiabilité des transactions mobiles. Dans ce contexte, une solution de supervision dédiée aux transactions financières mobiles devient essentielle pour détecter rapidement les anomalies et optimiser les revenus. Découvrez comment S-ONE MFS, la plateforme de surveillance Mobile Financial Services de Synaptique, fournit des tableaux de bord et des indicateurs clés (KPIs) qui aident les équipes opérationnelles, financières et commerciales à prendre des décisions plus rapides et plus éclairées.
Qu’est-ce que S-ONE MFS et comment supporte-t-il la supervision Mobile Money ?
S-ONE MFS est la solution avancée de Mobile Financial Services (MFS) conçue par Synaptique pour les opérateurs télécoms. Face à l’adoption croissante du Mobile Money dans les marchés émergents et établis, il est devenu indispensable de garantir la fiabilité des transactions en temps réel.
La plateforme offre une visualisation des données en temps réel et historique, fournissant aux opérateurs des insights exploitables sur l’ensemble des activités Mobile Money : transferts entre particuliers, paiements de factures, recharges de crédit, transactions auprès des commerçants, etc.
Note importante : S-ONE MFS se concentre sur la performance opérationnelle et l’intelligence transactionnelle. Il ne comporte pas de fonctionnalités de lutte contre le blanchiment (AML) ou de financement du terrorisme (CTF). C’est avant tout un outil d’observabilité, avec des analyses robustes, des alertes automatiques et des tableaux de bord BI dédiés à l’assurance revenus et à l’optimisation du service.
Pour un aperçu complet des fonctionnalités et bénéfices :
- Téléchargez la brochure
- Planifiez un appel
Quels indicateurs clés (KPIs) S-ONE MFS peut-il suivre ?
S-ONE MFS propose un ensemble riche de KPIs pour offrir une visibilité granulaire sur les services Mobile Money :
- Total des transactions
Suivi du nombre de transactions réalisées sur des périodes définies (quotidien, hebdomadaire, mensuel).
→ Mesure de l’adoption et des tendances de croissance. - Taux de succès des transactions
Pourcentage de transactions réussies versus celles échouées.
→ Permet d’identifier la fiabilité du service et les problèmes techniques. - Valeur moyenne des transactions
Calcul de la valeur moyenne de toutes les transactions validées.
→ Donne des indications sur le comportement des utilisateurs et le panier moyen. - Volume par canal
Répartition des transactions selon le canal d’accès (application mobile, USSD, SMS).
→ Met en évidence les préférences utilisateurs et les canaux sous-performants. - Temps de traitement
Surveillance de la durée moyenne nécessaire pour traiter une transaction.
→ Permet de détecter les goulets d’étranglement et d’améliorer la performance. - Taux d’erreurs/échecs
Fréquence des transactions échouées suite à une erreur système ou un incident technique.
→ Crucial pour la gestion proactive des incidents. - Activité utilisateur
Fréquence d’utilisation, nombre moyen de transactions par utilisateur, activité des portefeuilles.
→ Utile pour analyser l’engagement et optimiser les services. - Nombre d’alertes
Comptabilisation des alertes générées par le système suite à des anomalies transactionnelles.
→ Permet de réagir immédiatement aux comportements suspects. - Disponibilité du système / Uptime
Mesure du temps de disponibilité de la plateforme pour garantir une accessibilité constante des utilisateurs.
→ Indispensable pour le respect des SLA et la satisfaction clients.
Comment sont structurés les tableaux de bord dans S-ONE MFS ?
Les tableaux de bord de S-ONE MFS sont entièrement personnalisables et conçus pour différents services : exploitation réseau, finance, support client, etc. :
1. Tableaux de bord de supervision opérationnelle
- Vue en temps réel du nombre de transactions et des taux de succès
- Alertes sur dégradation ou interruption de service
2. Tableaux de bord d’analyse des revenus
- Répartition visuelle des revenus par type de service (transferts, recharges, paiements)
- Rentabilité des réseaux d’agents
3. Tableaux de bord d’utilisation et d’adoption
- Répartition géographique de l’usage Mobile Money
- Taux d’adoption par segment d’utilisateurs
4. Tableaux de bord de détection d’anomalies
- Cartes thermiques et graphiques des comportements transactionnels anormaux
- Filtres pour investiguer par MSISDN, type de transaction ou plage temporelle
Comment S-ONE MFS permet aux opérateurs de prendre des décisions plus rapides et plus avisées ?
S-ONE MFS offre :
- Alertes en temps réel sur échecs de transactions ou pics de volume
- Analyses historiques pour identifier tendances et problèmes de performance au fil du temps
- Insights segmentés pour adapter l’offre selon le comportement ou la région
- Rapports exportables pour la direction, les équipes techniques ou les partenaires externes
Ces informations permettent aux opérateurs de :
- Garantir une disponibilité maximale et la continuité du service
- Améliorer l’expérience client en corrigeant rapidement les incidents
- Optimiser la couverture des agents et la liquidité des portefeuilles
- Comprendre le comportement des utilisateurs et lancer de nouveaux services à forte valeur
Pourquoi S-ONE MFS est-il un outil stratégique pour les opérateurs télécom ?
Contrairement aux solutions bancaires classiques, S-ONE MFS a été développé pour les opérateurs télécom :
- Déploiement rapide grâce à des API flexibles
- Scalabilité pour accompagner la croissance des volumes transactionnels
- Sécurité “telecom-grade” et gestion des données conforme
De plus, les opérateurs peuvent se concentrer sur la qualité de l’expérience client et la surveillance des revenus sans devoir gérer la complexité réglementaire liée aux outils AML/CTF.
Découvrir S-ONE MFS en action ?
Notre équipe se tient à votre disposition pour vous montrer comment S-ONE MFS s’adapte à vos besoins :
- Téléchargez la brochure pour un aperçu approfondi des fonctionnalités
- Réservez un appel pour planifier une démonstration personnalisée
Rendez la supervision Mobile Money plus intelligente, plus rapide et plus centrée sur l’opérateur avec S-ONE MFS.
Upcoming Events
- All
- Webinar
- Conference
- Expo
novembre 13, 2024
Webinar Preventing Revenue Leakage Core vs. Intelligent Network Reconciliation
join us for an insightful live session on " Core…
Read Moreseptembre 14, 2024
Synaptique at GITEX GLOBAL 2024
Join our team at GITEX Global from October 18 to 24,…
Read Moreseptembre 5, 2024
Synaptique at TARS Africa 2024 in Casablanca 12-13 September
Join us at TARS Africa 2024 in Casablanca 12-13 September,…
Read More